Table of Contents
ToggleAbstract
The word has been changed a lot in the last couple of decades. Instead of simply dealing with local or regional concerns, many businesses now have to think about global markets and logistics. Many companies have facilities spread out across the country or around the world, and there is one thing that all of them need: A way to maintain fast, secure and reliable communications wherever their offices are.
As the popularity of the Internet grew, Businesses turned to it as a means of extending their own network. Now many companies are creating their own VPN (virtual private network) to accommodate the needs of remote employees and distance offices.
A VPN is a private network that uses a public network (usually the Internet) to connect remote sites or users together. Instead of using a dedicated, real-world connection such as leased line, a VPN uses “virtual” connections routed through the Internet from the company’s private network to the remote site or employee.
Here, we include common uses of VPN, types of VPN, VPN Security, VPN technology, VPN examples etc.
Introduction
The world has changed a lot in the last couple of decades. Instead of simply dealing with local or regional concerns, many businesses now have to think about global markets and logistics. Many companies have facilities spread out across the country or around the world, and there is one thing that all of them need: A way to maintain fast, secure and reliable communications wherever their offices are.
Until fairly recently, this has meant the use of leased lines to maintain a wide area network (WAN). Leased lines, ranging from ISDN (integrated services digital network, 128 Kbps) to OC3 (Optical Carrier-3, 155 Mbps) fiber, provided a company with a way to expand its private network beyond its immediate geographic area. A WAN had obvious advantages over a public network like the Internet
When it came to reliability, performance and security. But maintaining a WAN, particularly when using leased lines, can become quite expensive and often rises in cost as the distance between the offices increases.
As the popularity of the Internet grew, businesses turned to it as a means of extending their own networks. First came intranets, which are password-protected sites designed for use only by company employees. Now, many companies are creating their own VPN (virtual private network) to accommodate the needs of remote employees and distant offices.
Comparison with other Current System
Basically, a VPN is a private network that uses a public network (usually the Internet) to connect remote sites or users together. Instead of using a dedicated, real-world connection such as leased line, a VPN uses “virtual” connections routed through the Internet from the company’s private network to the remote site or employee. In this article, you will gain a fundamental understanding of VPNs, and learn about basic VPN components, technologies, tunneling and security.
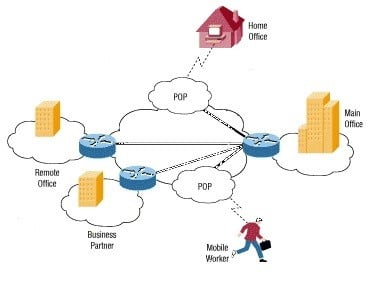
Common Uses of VPNs
The next few subsections describe the more common VPN configurations in more detail.
Remote Access Over the Internet
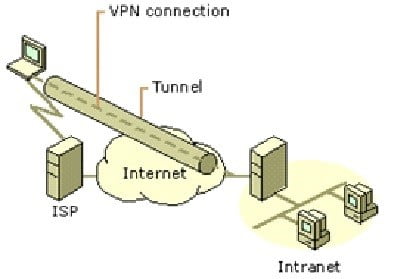
VPNs provide remote access to corporate resources over the public Internet, while maintaining privacy of information. Figure 2 shows a VPN connection used to connect a remote user to a corporate intranet.
Using a VPN connection to connect a remote client to a private intranet Rather than making a long distance (or 1-800) call to a corporate or outsourced network access server (NAS), the user calls a local ISP. Using the connection to the local ISP, the VPN software creates a virtual private network between the dial-up user and the corporate VPN server across the Internet.
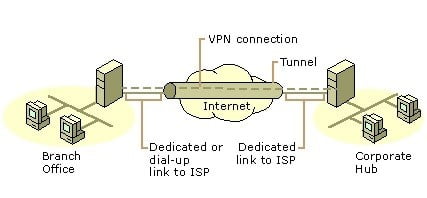
Connecting Networks Over the Internet
There are two methods for using VPNs to connect local area networks at remote sites:
- Using dedicated lines to connect a branch office to a corporate LAN. Rather than using an expensive long-haul dedicated circuit between the branch office and the corporate hub, both the branch office and the corporate hub routers can use a local dedicated circuit and local ISP to connect to the Internet. The VPN software uses the local ISP connections and the Internet to create a virtual private network between the branch office router and corporate hub router.
- Using a dial-up line to connect a branch office to a corporate LAN. Rather than having a router at the branch office make a long distance (or 1-800) call to a corporate or outsourced NAS, the router at the branch office can call the local ISP. The VPN software uses the connection to the local ISP to create a VPN between the branch office router and the corporate hub router across the Internet.
Using a VPN connection to connect two remote sites. In both cases, the facilities that connect the branch office and corporate offices to the Internet are local. The corporate hub router that acts as a VPN server must be connected to a local ISP with a dedicated line. This VPN server must be listening 24 hours a day for incoming VPN traffic.
Connecting Computers over an Intranet
In some corporate internetworks, the departmental data is so sensitive that the department’s LAN is physically disconnected from the rest of the corporate internetwork. Although this protects the department’s confidential information, it creates information accessibility problems for those users not physically connected to the separate LAN.
In some corporate internetworks, the departmental data is so sensitive that the department’s LAN is physically disconnected from the rest of the corporate internetwork. Although this protects the department’s confidential information, it creates information accessibility problems for those users not physically connected to the separate LAN.
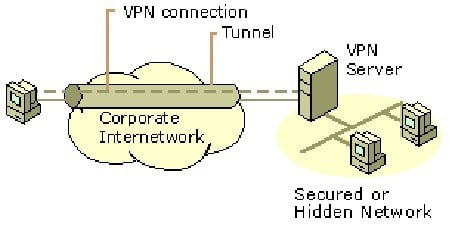
VPNs allow the department’s LAN to be physically connected to the corporate internetwork but separated by a VPN server. The VPN server is not acting as a router between the corporate internet work and the department LAN. A router would connect the two networks, allowing everyone access to the sensitive LAN. By using a VPN, the network administrator can ensure that only those users on the corporate internet work who have appropriate credentials (based on a need-to-know policy within the company) can establish a VPN with the VPN server and gain access to the protected resources of the department. Additionally, all communication across the VPN can be encrypted for data confidentiality. Those users who do not have the proper credentials cannot view the department LAN.
What Makes A VPN?
A well-designed VPN can greatly benefit a company. For example, it can:
Extend geographic connectivity
- Improve security
- Reduce operational costs versus traditional WAN
- Reduce transit time and transportation costs for remote users
- Improve productivity
- Simplify network topology
- Provide global networking opportunities
- Provide telecommuter support
- Provide broadband networking compatibility
- Provide faster ROI (return on investment) than traditional WAN
Features are needed in a well-designed VPN. It should incorporate:
- Security
- Reliability
- Scalability
- Network management
- Policy management
There are three types of VPN. In the next couple of sections, we’ll describe them in detail
Types of VPN
Site-to-Site VPN (LAN-to-LAN VPNs)
Through the use of dedicated equipment and large-scale encryption, a company can connect multiple fixed sites over a public network such as the Internet. Site-to-site VPNs can be one of two types:
Intranet-based – If a company has one or more remote locations that they wish to join in a single private network, they can create an intranet VPN to connect LAN to LAN.
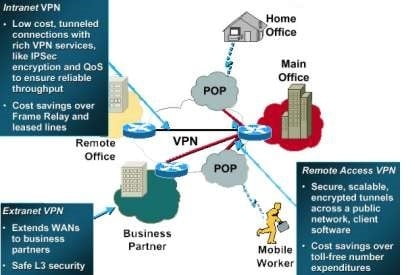
Extranet-based – When a company has a close relationship with another company (for example, a partner, supplier or customer), they can build an extranet VPN that connects LAN to LAN, and that allows all of the various companies to work in a shared
Remote access VPNs
That allows individual dial – up users to connect to a central site across the Internet or other public network service in a secure way. Remote access VPNs are sometimes referred to as dial VPNs.
Extranet VPNs
That allows secure connections with business partners, suppliers and customers for the purpose of e-commerce. Extranet VPNs are the extension of Internet VPNs with the addition of firewalls to protect the internal network.
Example:-
Analogy: Each LAN is an Island. Imagine that you live on an island in a huge ocean. There are thousands of other islands all around you, some very close and others farther away. The normal way to travel is to take a ferry from your island to whichever island you wish to visit. Of course, traveling on a ferry means that you have almost no privacy. Anything you do can be seen by someone else.
Let’s say that each island represents a private LAN and the ocean is the Internet. Traveling by ferry is like connecting to a Web server or other device through the Internet. You have no control over the wires and routers that make up the Internet, just like you have no control over the other people on the ferry. This leaves you susceptible to security issues if you are trying to connect between two private networks using a public resource.
Continuing with our analogy, your island decides to build a bridge to another island so that there is easier, more secure and direct way for people to travel between the two. It is expensive to build and maintain the bridge, even though the island you are connecting with is very close. But the need for a reliable, secure path is so great that you do it anyway. Your island would like to connect to a second island that is much farther away but decides that the cost are simply too much to bear.
This is very much like having a leased line. The bridges (leased lines) are separate from the ocean (Internet), yet are able to connect the islands (LANs). Many companies have chosen this route because of the need for security and reliability in connecting their remote offices. However, if the offices are very far apart, the cost can be prohibitively high — just like trying to build a bridge that spans a great distance.
So how does VPN fit in? Using our analogy, we could give each inhabitant of our islands a small submarine. Let’s assume that your submarine has some amazing properties:
- It’s fast.
- It’s easy to take with you wherever you go.
- It’s able to completely hide you from any other boats or submarines.
- It’s dependable.
- It costs little to add additional submarines to your fleet once the first is purchased.

Although they are traveling in the ocean along with other traffic, the inhabitants of our two islands could travel back and forth whenever they wanted to with privacy and security. That’s essentially how a VPN works. Each remote member of your network can communicate in a secure and reliable manner using the Internet as the medium to connect to the private LAN. A VPN can grow to accommodate more users and different locations much easier than a leased line. In fact, scalability is a major advantage that VPNs have over typical leased lines. Unlike with leased lines, where the cost increases in proportion to the distances involved, the geographic locations of each office matter little in the creation of a VPN.
VPN Security
A well-designed VPN uses several methods for keeping your connection and data secure:
- Firewalls
- Encryption
- AAA Server
In the following sections, we’ll discuss each of these security methods. We’ll start with the firewall.
Firewalls
A firewall provides a strong barrier between your private network and the Internet. You can set firewalls to restrict the number of open ports, what type of packets are passed through and which protocols are allowed through.
Some VPN products, such as Cisco’s 1700 routers, can be upgraded to include firewall capabilities by running the appropriate Cisco IOS on them. You should already have a good firewall in place before you implement a VPN, but a firewall can also be used to terminate the VPN sessions.
Encryption
Encryption is the process of taking all the data that one computer is sending to another and encoding it into a form that only the other computer will be able to decode. Most computer encryption systems belong in one of two categories:
- Symmetric-key encryption
- Public-key encryption
In symmetric-key encryption, each computer has a secret key (code) that it can use to encrypt a packet of information before it is sent over the network to another computer. Symmetric-key requires that you know which computers will be talking to each other so you can install the key on each one. Symmetric-key encryption is essentially the same as a secret code that each of the two computers must know in order to decode the information. The code provides the key to decoding the message. Think of it like this: You create a coded message to send to a friend in which each letter is substituted with the letter that is two down from it in the alphabet. So “A” becomes “C,” and “B” becomes “D”. You have already told a trusted friend that the code is “Shift by 2”. Your friend gets the message and decodes it. Anyone else who sees the message will see only nonsense.
The sending computer encrypts the document with a symmetric key, then encrypts the symmetric key with the public key of the receiving computer. The receiving computer uses its private key to decode the symmetric key. It then uses the symmetric key to decode the document.
Public-key encryption uses a combination of a private key and a public key. The private key is known only to your computer, while the public key is given by your computer to any computer that wants to communicate securely with it. To decode an encrypted message, a computer must use the public key, provided by the originating computer, and its own private key. A very popular public-key encryption utility is called Pretty Good Privacy (PGP), which allows you to encrypt almost anything. You can find out more about PGP at the PGP site.
AAA Servers
AAA (authentication, authorization and accounting) servers are used for more secure access in a remote-access VPN environment. When a request to establish a session comes in from a dial-up client, the request is proxied to the AAA server. AAA then checks the following:
Who you are (authentication)
- What you are allowed to do (authorization)
- What you actually do (accounting)
The accounting information is especially useful for tracking client use for security auditing, billing or reporting purposes.
Technologies
Depending on the type of VPN (remote-access or site-to-site), you will need to put in place certain components to build your VPN. These might include:
- Desktop software client for each remote user
- Dedicated hardware such as a VPN concentrator or secure PIX firewall
- Dedicated VPN server for dial-up services
- NAS (network access server) used by service provider for remote-user VPN access
- VPN network and policy-management center
Because there is no widely accepted standard for implementing a VPN, many companies have developed turn-key solutions on their own. In the next few sections, we’ll discuss some of the solutions offered by Cisco, one of the most prevalent networking technology companies.
VPN Concentrator
Incorporating the most advanced encryption and authentication techniques available, Cisco VPN concentrators are built specifically for creating a remote-access VPN. They provide high availability, high performance and scalability and include components, called scalable encryption processing (SEP) modules, that enable users to easily increase capacity and throughput. The concentrators are offered in models suitable for everything from small businesses with up to 100 remote-access users to large organizations with up to 10,000 simultaneous remote users.
An amazing piece of technology, the PIX (private Internet exchange) firewall combines dynamic network address translation, proxy server, packet filtration, firewall and VPN capabilities in a single piece of hardware.
Instead of using Cisco IOS, this device has a highly streamlined OS that trades the ability to handle a variety of protocols for extreme robustness and performance by focusing on IP.
Tunneling
Most VPNs rely on tunneling to create a private network that reaches across the Internet. Essentially, tunneling is the process of placing an entire packet within another packet and sending it over a network. The protocol of the outer packet is understood by the network and both points, called tunnel interfaces, where the packet enters and exits the network.
Tunneling requires three different protocols:
- Carrier protocol – The protocol used by the network that the information is traveling over
- Encapsulating protocol – The protocol (GRE, IPSec, L2F, PPTP, L2TP) that is wrapped around the original data
- Passenger protocol – The original data (IPX, NetBeui, IP) being carried
Tunneling has amazing implications for VPNs. For example, you can place a packet that uses a protocol not supported on the Internet (such as NetBeui) inside an IP packet and send it safely over the Internet. Or you could put a packet that uses a private (non-routable) IP address inside a packet that uses a globally unique IP address to extend a private network over the Internet.
Tunneling: Site-to-Site
In a site-to-site VPN, GRE (generic routing encapsulation) is normally the encapsulating protocol that provides the framework for how to package the passenger protocol for transport over the carrier protocol, which is typically IP-based. This includes information on what type of packet you are encapsulating and information about the connection between the client and server. Instead of GRE, IPSec in tunnel mode is sometimes used as the encapsulating protocol. IPSec works well on both remote-access and site-to-site VPNs. IPSec must be supported at both tunnel interfaces to use.
Tunneling: Remote-Access
In a remote-access VPN, tunneling normally takes place using PPP. Part of the TCP/IP stack, PPP is the carrier for other IP protocols when communicating over the network between the host computer and a remote system. Remote-access VPN tunneling relies on PPP.
Each of the protocols listed below were built using the basic structure of PPP and are used by remote-access VPNs.
- L2F (Layer 2 Forwarding) – Developed by Cisco, L2F will use any authentication scheme supported by PPP.
- PPTP (Point-to-Point Tunneling Protocol) – PPTP was created by the PPTP Forum, a consortium which includes US Robotics, Microsoft, 3COM, Ascend and ECI Telematics. PPTP supports 40-bit and 128-bit encryption and will use any authentication scheme supported by PPP.
- L2TP (Layer 2 Tunneling Protocol) – L2TP is the product of a partnership between the members of the PPTP Forum, Cisco and the IETF (Internet Engineering Task Force). Combining features of both PPTP and L2F, L2TP also fully supports IPSec.
L2TP can be used as a tunneling protocol for site-to-site VPNs as well as remote-access VPNs. In fact, L2TP can create a tunnel between:
- Client and router
- NAS and router
- Router and router

Think of tunneling as having a computer delivered to you by UPS. The vendor packs the computer (passenger protocol) into a box (encapsulating protocol) which is then put on a UPS truck (carrier protocol) at the vendor’s warehouse (entry tunnel interface). The truck (carrier protocol) travels over the highways (Internet) to your home (exit tunnel interface) and delivers the computer. You open the box (encapsulating protocol) and remove the computer (passenger protocol). Tunneling is just that simple!
As you can see, VPNs are a great way for a company to keep its employees and partners connected no matter where they are.
Example of VPN
Remote access for employees
Remote access for Electronic, Inc. employees is deployed by using remote access VPN connections across the Internet based on the settings configured in Common configuration for the VPN server and the following additional settings.
The following illustration shows the Electronic, Inc. VPN server that provides remote access VPN connections.
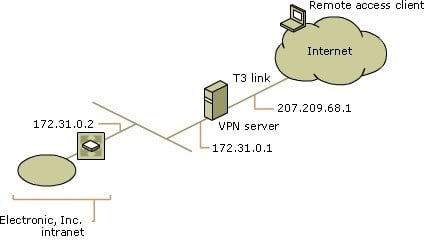
Domain configuration
For each employee that is allowed VPN access:
The remote access permission on the dial-in properties of the user account is set to Control access through Remote Access Policy The user account is added to the VPN_Users Active Directory group.
Remote access policy configuration
To define the authentication and encryption settings for remote access VPN clients, the following remote access policy is created:
Policy name: Remote Access VPN Clients
Conditions:
NAS-Port-Type is set to Virtual (VPN)
Windows-Groups is set to VPN_Users
Called-Station-ID is set to 207.209.68.
Permission is set to Grant remote access permission
Profile settings:
Authentication tab: Extensible Authentication Protocol is enabled and Smartcard or other certificate (TLS) is configured to use the installed computer certificate (also known as the machine certificate).
Microsoft Encrypted Authentication version 2 (MS-CHAP v2) and Microsoft Encrypted Authentication (MS-CHAP) are also enabled.
Encryption tab: Strong and Strongest are the only options that are selected.
The Called-Station-ID condition is set to the IP address of the Internet interface for the VPN server. Only tunnels initiated from the Internet are allowed. Tunnels initiated from the Electronic, Inc. intranet are not permitted. Electronic, Inc. users that require Internet access from the Electronic, Inc. intranet must go through the Electronic, Inc. proxy server (not shown), where Internet access is controlled and monitored.
PPTP-based remote access client configuration
The New Connection Wizard is used on client computers to create a VPN connection with the following setting:
Host name or IP address: vpn.electronic.microsoft.com
On the Networking tab, Type of dial-up server I am calling is set to Point-to-Point Tunneling Protocol (PPTP). This is done to provide better performance when connecting. When Type of dial-up server I am calling is set to Automatic, an Internet Protocol security (IPSec) security association (SA) for an Layer Two Tunneling Protocol (L2TP) connection is attempted first. By configuring the connection for PPTP, the IPSec SA for an L2TP connection is not attempted.
L2TP/IPSec remote access client configuration
The remote access computer logs on to the Electronic, Inc. domain using a LAN connection to the Electronic, Inc. intranet and receives a certificate through auto-enrollment. Then, the New Connection Wizard is used to create a VPN connection with the following setting
Host name or IP address: vpn.electronic.microsoft.com
The VPN connection settings are modified as follows:
On the Networking tab, Type of dial-up server I am calling is set to Layer-2 Tunneling Protocol (L2TP). When Type of dial-up server I am calling is set to Automatic, an IPSec SA for an L2TP connection is attempted first. If the IPSec SA is not successful, then a PPTP connection is attempted. In this case, the network administrator for Electronic, Inc. does not want remote access clients that are capable of establishing an L2TP connection to fall back to the PPTP connection.
On Windows Server 2003, Web Edition, and Windows Server 2003, Standard Edition, you can create up to 1,000 Point-to-Point Tunneling Protocol (PPTP) ports, and you can create up to 1,000 Layer Two Tunneling Protocol (L2TP) ports. However, Windows Server 2003, Web Edition, can accept only one virtual private network (VPN) connection at a time. Windows Server 2003, Standard Edition, can accept up to 1,000 concurrent VPN connections. If 1,000 VPN clients are connected, further connection attempts are denied until the number of connections falls below 1,000.
The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred.
Example of VPNs
On-Demand Branch Office
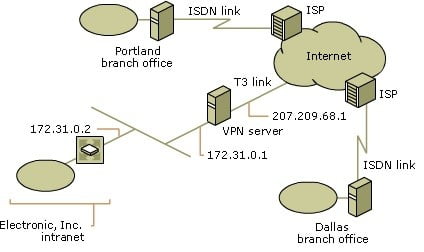
The Portland and Dallas branch offices of Electronic, Inc. are connected to the corporate office by using on-demand router-to-router VPN connections.
Both the Portland and Dallas offices contain a small number of employees who only need occasional connectivity with the corporate office. The routers running Windows Server 2003, Standard Edition, in the Portland and Dallas offices are equipped with an ISDN adapter that dials a local Internet service provider to gain access to the Internet, and then a router-to-router VPN connection is made across the Internet. When the VPN connection is not used for five minutes, the routers at the branch offices terminate the VPN connection.
The Dallas branch office uses the IP network ID of 192.168.28.0 with a subnet mask of 255.255.255.0. The Portland branch office uses the IP network ID of 192.168.4.0 with a subnet mask of 255.255.255.0.
To simplify the configuration, the VPN connection is a one-way initiated connection that is always initiated by the branch office router. For more
information, see One-way initiated demand-dial connections.
The following illustration shows the Electronic, Inc. VPN server that provides on-demand branch office connections.
To deploy on-demand router-to-router VPN connections to connect the Portland and Dallas branch offices to the corporate office based on the settings configured in Common configuration for the VPN server, the following additional settings are configured.
Domain configuration
For the VPN connection to the Dallas office, the user account VPN_Dallas is created with the following settings:
Password of nY7W{q8~=z3.
For the dial-in properties on the VPN_Dallas account, the remote access permission is set to Control access through Remote Access Policy, and the static route is 192.168.28.0 with a subnet mask of 255.255.255.0 is added
For the account properties on the VPN_Dallas account, the Password never expires account option is enabled.
The VPN_Dallas account is added to the VPN_Routers group.
For the VPN connection to the Portland office, the user account VPN_Portland is created with the following settings:
Password of P*4s=wq!Gx1.
For the dial-in properties on the VPN_Portland account, the remote access permission is set to Control access through Remote Access Policy, and the static route is 192.168.4.0 with a subnet mask of 255.255.255.0 is added
For the account properties on the VPN_Portland account, the Password never expires account option is enabled
The VPN_Portland account is added to the VPN_Routers group.
Remote access policy configuration
To define the authentication and encryption settings for the VPN routers, the following remote access policy is created:
Policy name: VPN Routers
Conditions:
NAS-Port-Type is set to Virtual (VPN)
Windows-Groups is set to VPN_Routers
Called-Station-ID is set to 207.209.68.1
Permission is set to Grant remote access permission.
Profile settings:
Authentication tab: Extensible Authentication Protocol is enabled and Smartcard or other certificate (TLS) is configured to use the installed computer certificate (also known as the machine certificate). Microsoft Encrypted Authentication version 2 (MS-CHAP v2) is also enabled
Encryption tab: Strong and Strongest are the only options that are selected.
The Called-Station-ID is set to the IP address of the Internet interface for the VPN server. Only tunnels initiated from the Internet are allowed. Tunnels initiated from the Electronic, Inc. intranet are not permitted. Electronic, Inc. users that require Internet access from the Electronic, Inc. intranet must go through the Electronic, Inc. proxy server (not shown), where Internet access is controlled and monitored.
Dial-up and VPNs with RADIUS
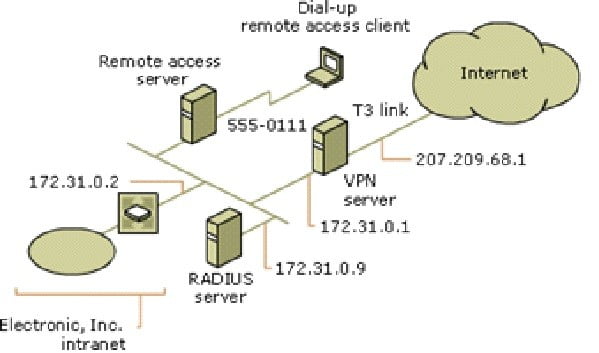
In addition to VPN-based remote access, the network administrator for Electronic, Inc. wants to provide modem-based dial-up remote access for employees of the New York office. All employees of the New York office belong to a Windows Server 2003 operating system group called NY_Employees. A separate remote access server running Windows Server 2003, Standard Edition, provides dial-up remote access at the phone number 555-0111. Rather than administer the remote access policies of both the VPN server and the remote access server separately, the network administrator is using a computer running Windows Server 2003, Standard Edition; Windows Server 2003, Enterprise Edition; or Windows Server 2003, Datacenter Edition; with Internet Authentication Service (IAS) as a RADIUS server. The IAS server has an IP address of 172.31.0.9 on the Electronic, Inc. extranet and provides centralized remote access authentication, authorization, and accounting for both the remote access server and the VPN server.
The following illustration shows the Electronic, Inc. RADIUS server that provides authentication and accounting for the VPN server and the remote access server.
Domain configuration
For each New York office employee that is allowed dial-up access, the remote access permission for the dial-in properties of the user account is set to Control access through Remote Access Policy.
Remote access policy configuration
Remote access policies must be modified in two ways:
The existing remote access policies that are configured on the VPN server running Windows Server 2003 must be copied to the IAS server.
A new remote access policy is added for dial-up remote access clients on the IAS server.
Copying the remote access policies
Once the VPN server running Windows Server 2003 is configured to use RADIUS authentication, the remote access policies stored on the VPN server are no longer used. Instead, the remote access policies stored on the IAS server running Windows Server 2003, Standard Edition; Windows Server 2003, Enterprise Edition; or Windows Server 2003, Datacenter Edition. Therefore, the current set of remote access policies is copied to the IAS server.
Creating a new remote access policy for dial-up remote access clients
To define the authentication and encryption settings for dial-up connections by employees of the New York office, the following remote access policy is created on the RADIUS server computer:
Policy name: Dial-Up for New York Employees
Conditions:
NAS-Port-Type is set to all types except Virtual (VPN)
Windows-Groups is set to NY_Employees
Permission is set to Grant remote access permission
Profile settings:
Authentication tab: Extensible Authentication Protocol is enabled and Smartcard or other certificate (TLS) is configured to use the installed computer certificate (also known as the machine certificate).
Microsoft Encrypted Authentication version 2 (MS-CHAP v2) and Microsoft Encrypted Authentication (MS-CHAP) are also enabled.
Encryption tab: All options are selected.
Radius configuration
To configure RADIUS authentication and accounting, the network administrator for Electronic, Inc. configures the following:
The RADIUS server is a computer running Windows Server 2003, Standard Edition; Windows Server 2003, Enterprise Edition; or Windows Server 2003, Datacenter Edition; and with IAS installed. IAS is configured for two RADIUS clients; the remote access server and the VPN server. For more information, see Internet Authentication Service and Add RADIUS clients.
The remote access server running a member of the Windows Server 2003 family is configured to use RADIUS authentication and accounting at the IP address of 172.31.0.9 and a shared secret. For more information, see Use RADIUS authentication and Use RADIUS accounting.
The VPN server running Windows Server 2003 is configured to use RADIUS authentication and accounting at the IP address of 172.31.0.9 and to use a shared secret. For more information, see Use RADIUS authentication and Use RADIUS accounting.
Dial-up remote access client configuration
The New Connection Wizard is used to create a dial-up connection with the following setting:
Phone number: 555-0111
The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred.
Conclusion
The VPN technology is the one of the best technology in the world for business network solutions. It is the more reliable & very secure technology than the other technology which is available before this technology.



To the electronicsforyou.in webmaster, Thanks for the informative and well-written post!